Matrix Intelligence
More than just a Cyber Search Engine
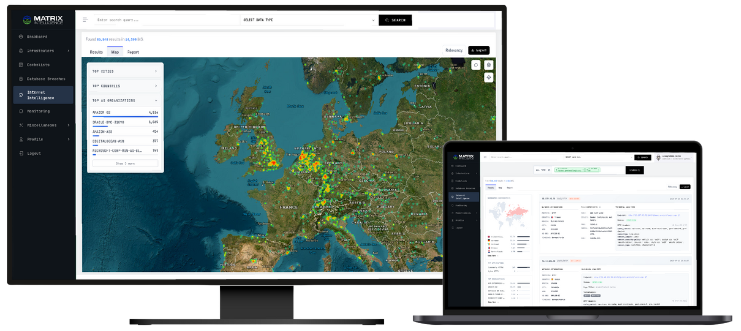
We specialize in collecting, aggregating and enriching extensive volumes of data from the Dark Web and comprehensive internet-wide probes, providing actionable insights to help secure your organization and stay ahead of emerging threats.
Matrix Intelligence
More than just a Cyber Search Engine
We specialize in collecting, aggregating and enriching extensive volumes of data from the Dark Web and comprehensive internet-wide probes, providing actionable insights to help secure your organization and stay ahead of emerging threats.

Our mission
We transform the “Hacker View” perspective into a proactive shield, providing banks, law enforcement, and enterprises with a single, unified platform that consolidates intelligence tools – allowing them to see through the attackers point of view.
We eliminate the need for multiple disconnected tools.
Everything you need for comprehensive cyber intelligence is integrated into one powerful platform.
Matrix Intelligence in Numbers
Devices compromised by Infostealers.
New Items Ingested Every 30 days.
Total Entries, growing by the day.
Our Intelligence Coverage
Use cases
Pricing
Early Adopter Pricing
These are exclusive Early Adopter rates. Prices will double as we scale our platform and expand our intelligence capabilities. Lock in these rates now.
STARTER
Essential threat intelligence for individual researchers
CHF 1,998 / month
- 500 queries per month
- Export credits
- 10 monitored items
- 1 user
RESEARCHER
Advanced capabilities for security professionals
CHF 3,998 / month
- 1,000 queries per month
- 100,000 export credits
- 25 monitored items
- 1 user
BUSINESS
Comprehensive solution for security teams
CHF 11,998 / month
- 4,000 queries per month
- 500,000 export credits
- 50 monitored items
- 5 users
CORPORATE
Enterprise intelligence for large organizations
CHF 31,998 / month
- 20,000 queries per month
- 3,000,000 export credits
- 300 monitored items
- 25 users
Pricing
These are exclusive Early Adopter rates. Prices will double as we scale our platform and expand our intelligence capabilities. Lock in these rates now.
STARTER
Essential threat intelligence for individual researchers
CHF 1,998 / month
- 500 queries per month
- Export credits
- 10 monitored items
- 1 user
RESEARCHER
Advanced capabilities for security professionals
CHF 3,998 / month
- 1,000 queries per month
- 100,000 export credits
- 25 monitored items
- 1 user
BUSINESS
Comprehensive solution for security teams
CHF 11,998 / month
- 4,000 queries per month
- 500,000 export credits
- 50 monitored items
- 5 users
CORPORATE
Enterprise intelligence for large organizations
CHF 31,998 / month
- 20,000 queries per month
- 3,000,000 export credits
- 300 monitored items
- 25 users
Blog
Leveraging Matrix Intelligence: A Guide to Internet Intelligence Search
Leveraging Matrix Intelligence: A Guide to Internet Intelligence Search Executive Summary This comprehensive guide demonstrates how to leverage Matrix Intelligence's Internet Intelligence Platform (IIP) for advanced cybersecurity reconnaissance and exposure...